This blog explained the initial setup. To continue adding more RADIUS client (i.e. Cisco devices), log on to the NPS server and fire up the Network Policy Server console.
1) Add RADIUS client
Right click on RADIUS client and click "New". Enter the name of device and the IP address. As a Cisco device may have multiple interfaces, I would prefer using the loopback address. Also, supply the pre-shared key between the server and the client.
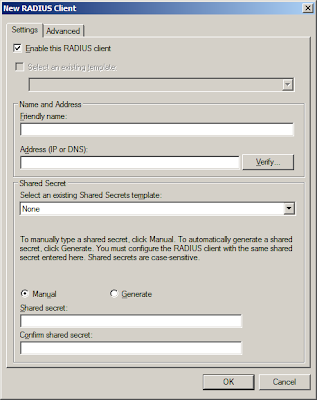
Note: Both IP addresses and the key must match. If not, authentication would fail.
2) Cisco Configuration
Cautious: Make sure you have another running line or console before you do this.
aaa new-model
#use radius login 1st. when time-out, use local password
#you may want to define your own list. Make sure the list in red must match the login vty below
aaa authentication login RadiusList group radius local
#make sure it matches the client IP address in the NAP server earlier
ip radius source-interface Loopback0
#replace the below brackets with your values
radius-server host [server_IP] auth-port 1812 acct-port 1813 timeout 5 key [your_key]
#apply authentication method
line vty 0 4
access-class MGMT_ACL in
logging synchronous
login authentication RadiusList
transport input ssh
3) Verifying & Troubleshooting
Try ssh into the device. If unsuccessful, check network connectivity from the client using "ping [server_IP] source loopback0". Run "debug radius" command and go to the event viewer of the server. For easy viewing, open up the Server Manager console and click on the "Network Policy Manager" where the login events are filtered automatically for you.
4) Change the prompt (Optional)
How do you know which are the devices use RADIUS or local authentication? Simple, just change the login & password prompts.
aaa authentication banner ^CAccess to this device is protected by NAP^C
aaa authentication password-prompt "NAP password:"
aaa authentication username-prompt "Your NAP id:"
I have many devices using RADIUS authentication (switches, routers, etc). What is the best practice for RADIUS keys? Should every device have a unique key? Is that really necessary? Why? I end up with a headache just keeping them straight.
ReplyDeleteI would suggest setting a group of devices having similar security level to share a common radius key. For example, you have a group of less critical devices, all of them can share a common password. For highly sensitive devices, probably an unique key for itself. It should strike a good balance between ease of manageability and security.
ReplyDeleteThanks for sharing this useful information. It will help the newbie in networking very much.
ReplyDeletesfp lr
Hi,
ReplyDeleteThank you for sharing this helpful information.
I love to read your blogs. Keep it up!
We offer network security system "Radius Authentication" to all type of businesses. If you or anyone else wants this security system for their business so please contact us for more information.